Version 2.4.49 of the Apache webserver is affected by a path traversal vulnerability. This caught a lot of people on the left foot. Well not those who protect their services with CRS. CRS has your back for this new exploit too - as very often.
There are a lot of proof of concept exploits for this vulnerability around now. All proof of concepts I saw work via hex encoding the dot-character as %2e. That means you can disguise a classical path traversal using dots as follows:
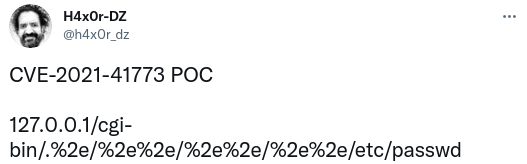
Apache 2.4.49 introduced a bug where it would fall for this trick.
CRS has two rules that will see through the ruse, though:
- 930100 Path Traversal Attack
- 930110 Path Traversal Attack
Both rules are paranoia level 1 rules. That means they are active in a default installation.
So while Apache administrators on 2.4.49 would need to rush to update to 2.4.50, admins using CRS for protection can schedule the necessary Apache update without any urgency: CRS buys you time!
Take away message: If you put anything on the web, make sure you protect it with a default ModSecurity / CRS WAF in front.
 Christian Folini / [@ChrFolini]
Christian Folini / [@ChrFolini]